Proactive measures

Misconceptions
- I trust my IT Supplier 100%
- My data is in the cloud so I am safe
- My anti-virus programme protects me sufficiently
- They have no business here, the money is with the big ones
- My data? No use to anyone
- We installed a firewall so we are completely safe
- Digital security is complex and expensive
- ...
Reality
Despite the ubiquitous presence of cybercrime, it keeps raining excuses when it comes to digital security. This is very strange, because you too no doubt have someone in your circle of acquaintances who has experienced a cyber incident by now. Digital safety is like safety while driving: you do everything you can to drive safely from point A to point B, but something can always happen on the way.
And then you want to be helped!
The high degree of automation in cybercrime means that it is not a question of IF a cyber incident will happen to you but rather WHEN

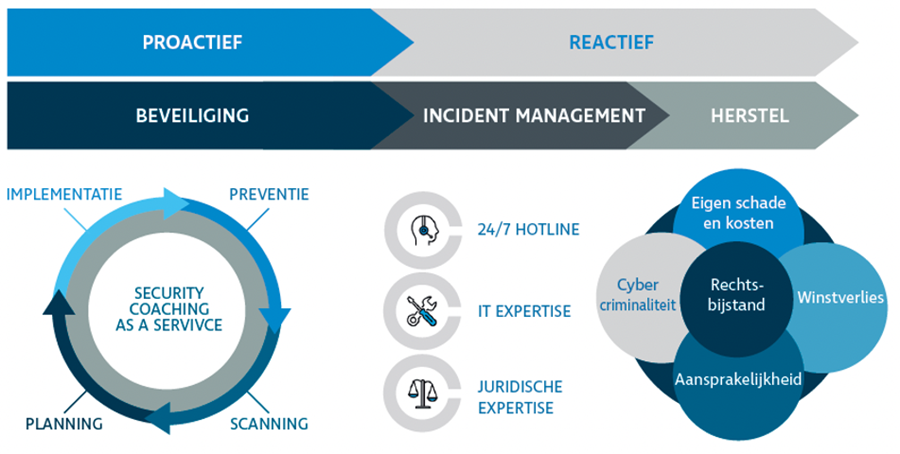
You realise you should do something but you don't know where or how to start? CyberContract helps your organisation bet on cyber security by applying a proactive approach. 100% safe does not exist, which is why you insure the residual risk in a reactive strategy; when things go wrong, you especially want to be helped. In this way, you make your organisation cyber resilient.
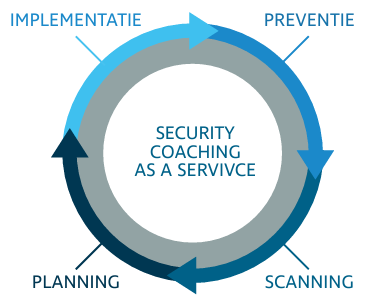
Prevention is the first step to secure the future of your business. Within this domain, there are simple steps you can take yourself, while other measures require more insight and planning. Our CyberSecurity Coach will map out with you which steps it is best to take first, and which measures require more detailed planning with various stakeholders.
Prevention
Not every step in security needs to cost (a lot of) money; there are simple measures that can immediately provide a lot of cyber security. By investing wisely in prevention, obvious tragedies can be avoided.
Scanning
We map out which digital windows and doors of your business are open, so you can see how a cybercriminal is looking at your business. We can equally do this from an internal perspective, performing essential security checks on your devices to ensure that only secure devices are allowed to use business applications.
Planning
From that scanning, we obtain a lot of valuable information where we turn the actions to be taken into a plan of action written to the size of your business.
Implementation
The implementation of these actions can of course be carried out by your existing IT partner, but CyberContract has a network of Trusted Partners around which we can confidently entrust our clients.