Committing to your company's cyber resilience is an absolute must today. Yet we understand that cybersecurity can be a very vast and complex topic, and that's why you can count on us. Insuring your cyberincidents does not work without working on your company's cyber safety. With the different steps we provide in cybersecurity, you are setting the right path towards being a cyber resilient company.
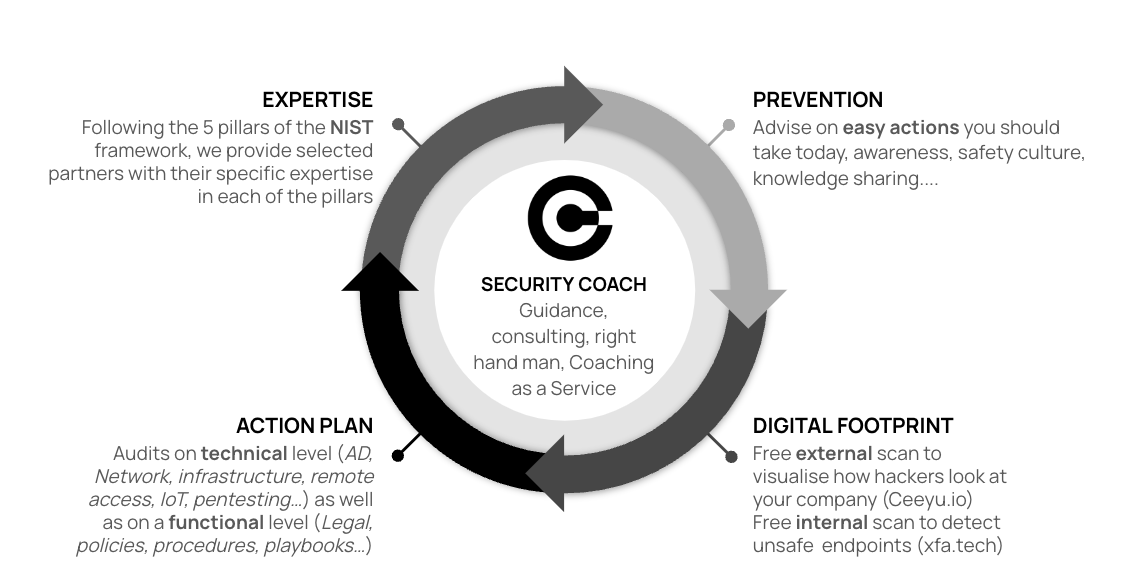

We want our customers to be safe, that's a first priority. Prevention is the first step in securing your company's future. Within this domain of prevention, there are steps you can take yourself today.
- → Actions you should take today additionally to our 10 step action list
- ♦ Use MFA
- ♦ Use different and strong passwords everywhere. Use a Password Manager to manage.
- ♦ Continuously work on Security Awareness
- → Extended lists of actions
- ♦ Work with frameworks like the CCB CyberFundamentals Framework; CyFun
- ♦ Use VLAIO subsidized CyberSecurity Improvement tracks

When we leave our houses, offices we faithfully close our windows and doors. We all know the concepts of keys, alarm codes, badges, locks... The digital world also has digital windows and doors, but there are so many, and they all have their own ways of being open or closed, we cannot expect everyone to know of the exsistence of these digital doors, let alone how to close them.
Therefore we provide FREE technical scans to all our customers to visualize these open digital doors and windows
- → Free EXTERNAL scan to see which digital windows and doors are open at your company
- ♦ This is how hackers look at your company; the scan reveals how easy hackers can intrude your company.
- ♦ We do this by relying on the expertise of our trusted partner Ceeyu.
- Ceeyu's SaaS platform identifies IT and network vulnerabilities for your company and your supply chain (Third Party Risk Management or TPRM) by combining automated scans (digital footprint mapping, attack surface scanning and cybersecurity risk ratings) with online questionnaire-based risk assessments.
- → Free INTERNAL scan to see which devices in your company are unsafe
- ♦ In a context where remote working with a Bring Your Own Device is standard, the number of possible open digital doors grows exponentially. Check wehter the devices accessing your network your applications are safe enough to do so. Do not let BYOD result in Bring Your Own Disaster!
- ♦ For this type of scanning we are happy to be workign woth XFA, our trusted partner ensuring only safe devices can access your business applications.
- XFA requests proof of security from all devices during authentication at compatible applications (SAMLv2, Oauth2 & custom integration), followed by access acceptance or rejection.

Whilst the scans work on a non invasive approach, with audits we really deepdive into your organisation.
- → TECHNICAL
- ♦ We provide full audits of your IT environments.
- ◊ Simple AD (Active Directory) checkup. You might be surprised on the number of misconfigurations here.
- ◊ Backup scenario's, disaster recovery approach, RBAC (Role Based Access Control), SOC implementation, SIEM...
- ◊ Pentesting, vulnerability scans for OnPrem software, cloud, webapplication, API's...
- ♦ We provide full audits of your IT environments.
- → FUNCTIONAL
- ♦ What procedures and policies are in place; Internet Usage Policy, BYOD policy, Business Continuity plan...
- ♦ Are these procedures and policies up to date, testing...
- → LEGAL
- ♦ Do the contracts you have with your customers, suppliers, partners... contain the necessary and correct wordings?
- ♦ Are you GDPR compliant, are you subject to NIS2, DORA...

In any of the areas of cybersecurity we provide selected partners who can assist you with their speciality. Following the 5 pillars of the NIST framework, we have a selected partner network: ranging from audits, to awareness training, phishing simulators, monitoring and detection partners, and specialists in response and recovery.

We do realise cybersecurity can be a very complex and technical topic. The misconception on cybersecurity is that it is very expensive and only for the multinationals. This is exactly the point where our cybersecurity coach can help. With a clear view on Return On Investment, we guide you in the steps you need to take in order to become a cyber resilient company.
For any of the services contact us!