The fact that more and more companies are moving their IT infrastructure to the "cloud" is more than a good move. No more servers under the desk suddenly shutting down with a wrong turn of the chair, no more interrupted well-deserved Friday night aperitifs to go restart the servers after the cleaning lady looked for a free outlet, and most importantly no more servers falling months behind on critical (security) updates.

Cloud software
The modern packages for accounting, CRM, ERP, collaboration ... are in the cloud today. You may also be using something from a cloud platform today; something internationally known or locally developed. Software manufacturers themselves take care of the entire server infrastructure (security, updates, upgrades, monitoring...), which is a very welcome relief for your organization.
Users like you and me put our most critical and confidential business data in those cloud platforms, which are usually secured with a username and password, and in the best case you use MFA (MultiFactor Authentication; authenticating using multiple factors than username and password alone, which is thus by definition more secure). If you do not yet use MFA, do so as soon as possible, as this makes it much more difficult for hackers to penetrate. But unfortunately, not impossible...
Everything looked legitimate!
Suppose your company's mail-system is configured with one of those big known cloud providers. Easy, simple to configure, and most importantly, much more secure than that under-the-office mail server you had to keep running yourself. Your accounting data is stored securely and encrypted in an online accounting package, sales reps track their sales cycle in a cloud-based CRM system, collaboration is also done efficiently in the cloud. Everything is also securely set up with SSO (Single Sign On) so you only have to log in once for the different platforms.
One day, the administrative assistant (who puts the incoming invoices in the accounting package) receives an e-mail from that well-known cloud provider, informing him that his password has expired; "Password Expiration Policy", a common practice which is recommended. The mail looks completely identical to all password reset mails that have always been sent, no difference at all. The administrative assistant pays attention and checks the sender, which is considered legitimate.
In good faith he clicks on the password reset link.
The screen he lands on looks pixel by pixel the same as he has always been used to. It's even(!) the "https" (secure) link he was made aware of during his last Phishing training. He resets the password, the page even requires additional authentication via the MFA app, and then just continues his work.
Authorized access
The next day, the administrative assistant arrives, wants to log into the accounting package to schedule vendor payments, but he can't with his new password. He tries with his old password, which strangely enough succeeds.
And then suddenly he sees payments to accounts unknown to him, large sums of money! Panic ensues, tens of thousands of euros have been transferred to foreign accounts. Completely shaken up, he calls the help desk of the accounting package, but they can only help him at 9 am. Once the helpdesk is on the line and explains the problem, a helpdesk ticket is registered. They are of good will and place the ticket in high priority, but the helpdesk specialist on duty is still stuck in a traffic jam.
Many anxious hours later there is back contact with the helpdesk, who tell him that they see no unauthorized actions in terms of access, everything seems normal. Payments were made at 6:30p.m., by the administrative assistant himself! So according to the system, there has been only authorized access.
So what happened here? Just reset password yesterday, even indicated with the MFA app that it was indeed him, and the reset link was even a secure "https" link!
This is a widely used principle officially called AiTM or MiTM; in full Attacker in The Middle or Man in The Middle. We won't dive into too much technical detail; there are plenty of articles on that. In a nutshell, a hacker wriggles into the communication you are conducting to, in this example, the cloud platform.
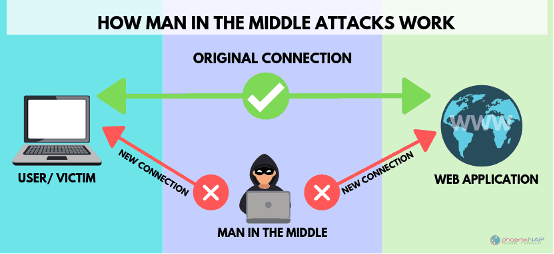
Step 1: The mail address
At first glance, the sender's name appears to be trustworthy. Usually, the real mail address is even hidden in many email programs (you only see the name, not the address) so you are not/can't be critical to identifying the real sender. If you look closely, you often see noticeable differences in the mail address, but often those differences are so minuscule that they appear legitimate. In this case, the mail address had a single discrepancy that was overlooked.
Step 2: The URL
Just checking, do you see the difference between URL 1 and URL 2?
URL 1: https://www.microsoftonline.com/resetpwd
URL 2: https://www.microsoftonlíne.com/resetpwd
Right, you already must be very observant, and especially not in a hurry to notice that difference. How about the next one?
URL 1: https://www.αpple.be
URL 2: https://www.apple.be
And when we hide those URLs behind text, you won't see anything at all, they are now both pointing to a different URL:
URL 1: Reset Password
URL 2: Reset Password
So it is not inconceivable that you and I could easily click on such links, especially since there was trust owing to a correct-looking sender. What happens here is that Cyrillic characters are used in the URL. An α instead of an a, an í instead of an i. Tricky, isn’t it?
Step 3: Authenticating.
But why, the administrative assistant had to use the MFA app to prove it was him, which is super secure, right?
Well, not quite so. What happened is he was shown a counterfeit page that was pixel by pixel identical to the real password reset page, no difference to be seen. But that page actually just captured the real password instead of performing a reset. Behind it, hackers then use cookies to retrieve and store that login information, and then use that login information to penetrate the accounting package.
The consequences
Tens of thousands of Euros gone, damage to reputation (customers and suppliers were not happy about it when they read this in the news), 3 days the company closed and a lot of lost time and costs to investigate how all this could happen.
Never 100% secure, assure!
So, then you think you are secure in the cloud, your IT Partner even configures MFA. Not only that, but you train your employees with Phishing programs and yet this can still happen? I can hear you thinking: then I better not do anything! Of course, the opposite is true. Just like with your house or business premises, you clsoe and lock all windows and doors after you leave. But does this ensure that you can guarantee that that house or business premises are 100% burglary safe?
No, 100% safe you can never guarantee.... Just like driving a car.
That's why it's so important, just like insuring your home, your business premises and your car without questions, to ensure your business continuity. And that it has already happened or is about to happen to you is a certainty. After all, Gartner predicts that 45% of all businesses will be hacked by 2025.
With Cyber Insurance, the company in this example could have called the 24/7 CyberContract hotline. That hotline could have arranged for IT specialists to come on site to find out how this happened, see if there were any further infections to be found, track down perpetrators (IT forensic services), and had assisted CyberContract in the legal aspects to help repair reputational damage (communication to customers and suppliers, possibly making it known to the government...).That process would surely have started much faster than having to wait for the traffic jammed help desk co-worker, and thus would probably not have taken 3 days. Above all, the costs (IT specialists, legal assistance, loss of profit...) of this whole story would have been covered with the CyberContract policy.
So don't wait until it's too late and insure your business continuity.
Sources: